OCSF Detection Finding Schema
The OCSF (Open Cybersecurity Schema Framework) Detection Finding schema is an open-source, vendor-agnostic standard for security telemetry. This schema:
- Adheres to industry best practices for security event formatting.
- Provides comprehensive attack categorization and findings.
- Includes comprehensive event context and metadata.
Understanding AlphaSOC's OCSF Detection Finding Events
AlphaSOC generates two types of OCSF events to efficiently represent multiple detections while maintaining compatibility with the OCSF specification. When a single source event triggers multiple detections (e.g., Detection X and Detection Y), the engine generates:
- One OCSF Finding Raw event: Contains the source event data and all associated detections.
- Multiple OCSF Finding events (one per detection): Represents individual detections without source data.
The diagram below shows how a single OCSF finding-raw event relates to multiple OCSF finding events through a shared correlation ID.
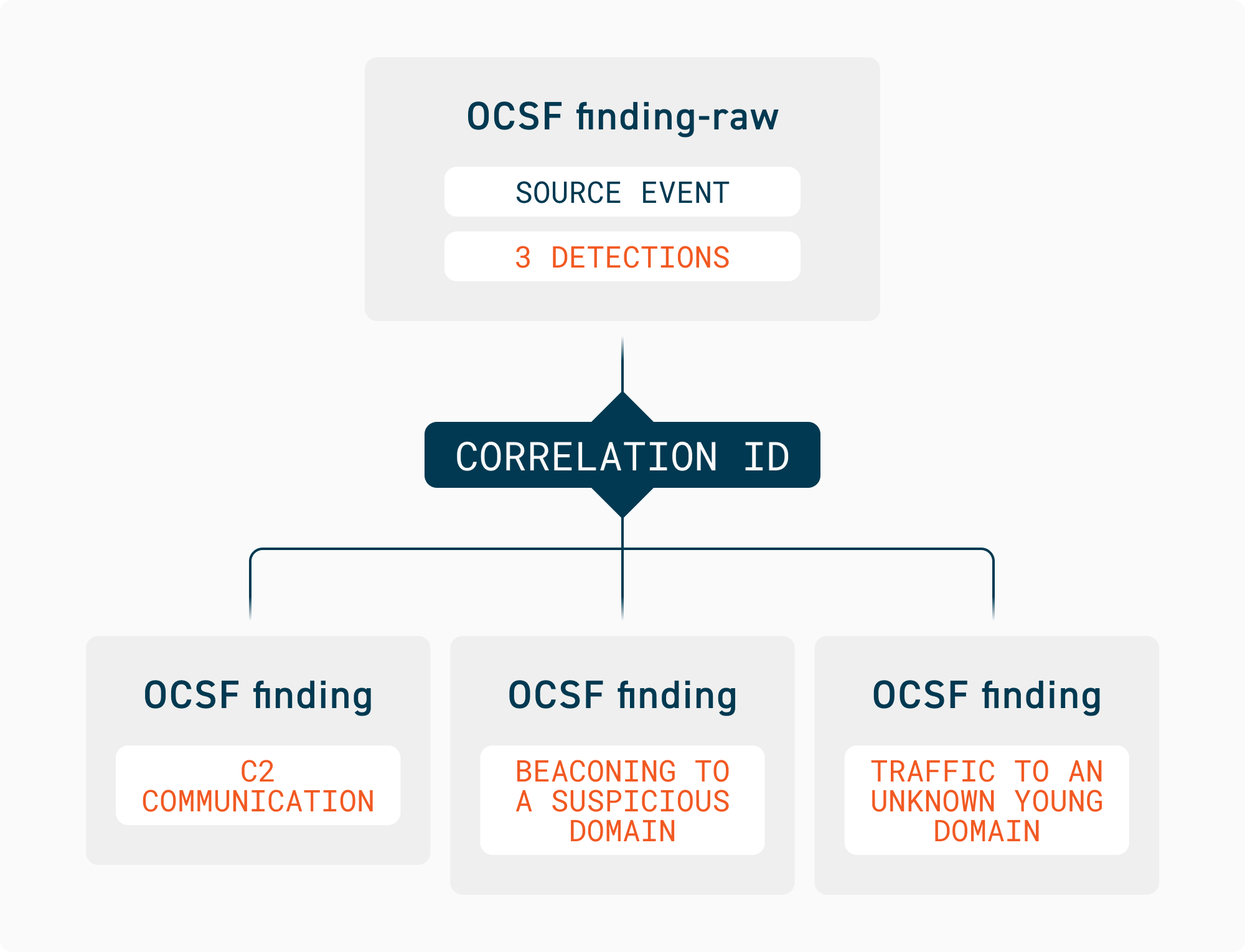
Both event types share the correlation ID, enabling easy tracking between source events and their corresponding findings. This split structure ensures proper rendering of individual detection attributes (title, severity, description) while preserving complete context for analysis and optimizing storage usage by avoiding duplicate source data across multiple findings.
OCSF Finding Raw
OCSF Finding Raw events contain comprehensive source event data along with all associated detections. These events serve as the primary reference point for full context analysis. For an example event, refer to the OCSF Finding Raw Example.
Key Fields
| Field | Description |
|---|---|
metadata.event_code | finding-raw |
metadata.correlation_uid | Link to OCSF Finding events |
finding_info.uid | Unique identifier for the specific finding-raw event |
finding_info.related_events[] | All generated detections and references to finding events |
evidences[] | Derived artifacts from source events |
count | Total source events (before sampling) |
severity | Maximum severity across all generated detections for this event |
OCSF Finding
OCSF Finding events represent individual detections with focused information about specific security findings. Each event contains a single detection's details without duplicating source event data. For an example event, refer to the OCSF Finding Example.
Key Fields
| Field | Description |
|---|---|
metadata.event_code | finding |
metadata.correlation_uid | Link to OCSF Finding Raw event |
finding_info.uid | Unique identifier for the specific finding and detection |
count | Total source events (before sampling) |
title | Detection title |
severity | Detection severity |
Correlation ID
The correlation ID links OCSF Finding Raw events with their corresponding OCSF Finding events, enabling two investigation approaches:
- From Finding event: Use correlation ID to access source event and related detections.
- From Finding Raw event: Use related events list to examine individual detections.
This bidirectional correlation allows efficient access to both detection details and source evidence during investigations.
Sampling
AlphaSOC groups findings logically and applies sampling within these groups. The
count field in both Finding Raw and Finding events indicates the total number
of source events in the logical group before sampling was applied.
Examples
OCSF Finding Raw Example
Below is an example of an OCSF Finding Raw event containing two detections
(suspicious_http_post and suspicious_domain) that share the same correlation
ID abe76dab-cd9c-4cb5-b6e2-9e15f7b46406:
{
"category_name": "Findings",
"category_uid": 2,
"class_name": "Detection Finding",
"class_uid": 2004,
"count": 1,
"metadata": {
"correlation_uid": "abe76dab-cd9c-4cb5-b6e2-9e15f7b46406",
"event_code": "finding-raw",
"labels": [
"domain:network"
],
"processed_time": 1754316019,
"processed_time_dt": "2025-08-04T14:00:19Z",
"product": {
"vendor_name": "AlphaSOC"
},
"profiles": [
"datetime"
],
"version": "1.5.0"
},
"observables": [
{
"name": "evidences[].http_request.url.hostname",
"type": "Hostname",
"type_id": 1,
"value": "ewubo.net"
},
{
OCSF Finding Example
Below is an example of an OCSF Finding event generated from the Finding Raw example above:
{
"category_name": "Findings",
"category_uid": 2,
"class_name": "Detection Finding",
"class_uid": 2004,
"count": 1,
"metadata": {
"correlation_uid": "abe76dab-cd9c-4cb5-b6e2-9e15f7b46406",
"event_code": "finding",
"labels": [
"domain:network"
],
"processed_time": 1754316019,
"processed_time_dt": "2025-08-04T14:00:19Z",
"product": {
"vendor_name": "AlphaSOC"
},
"profiles": [
"datetime"
],
"version": "1.5.0"
},
"observables": [
{
"name": "device.mac",
"type": "MAC Address",
"type_id": 3,
"value": "ca:2f:e2:4d:58:aa"
},
{