Rule Management
The Rule Management page lets you view and manage detection rules used by AlphaSOC to identify threats and anomalies in your environment. Here, you can explore AlphaSOC built-in detections and add your own custom Sigma rules to tailor detection coverage to your organization's specific needs.
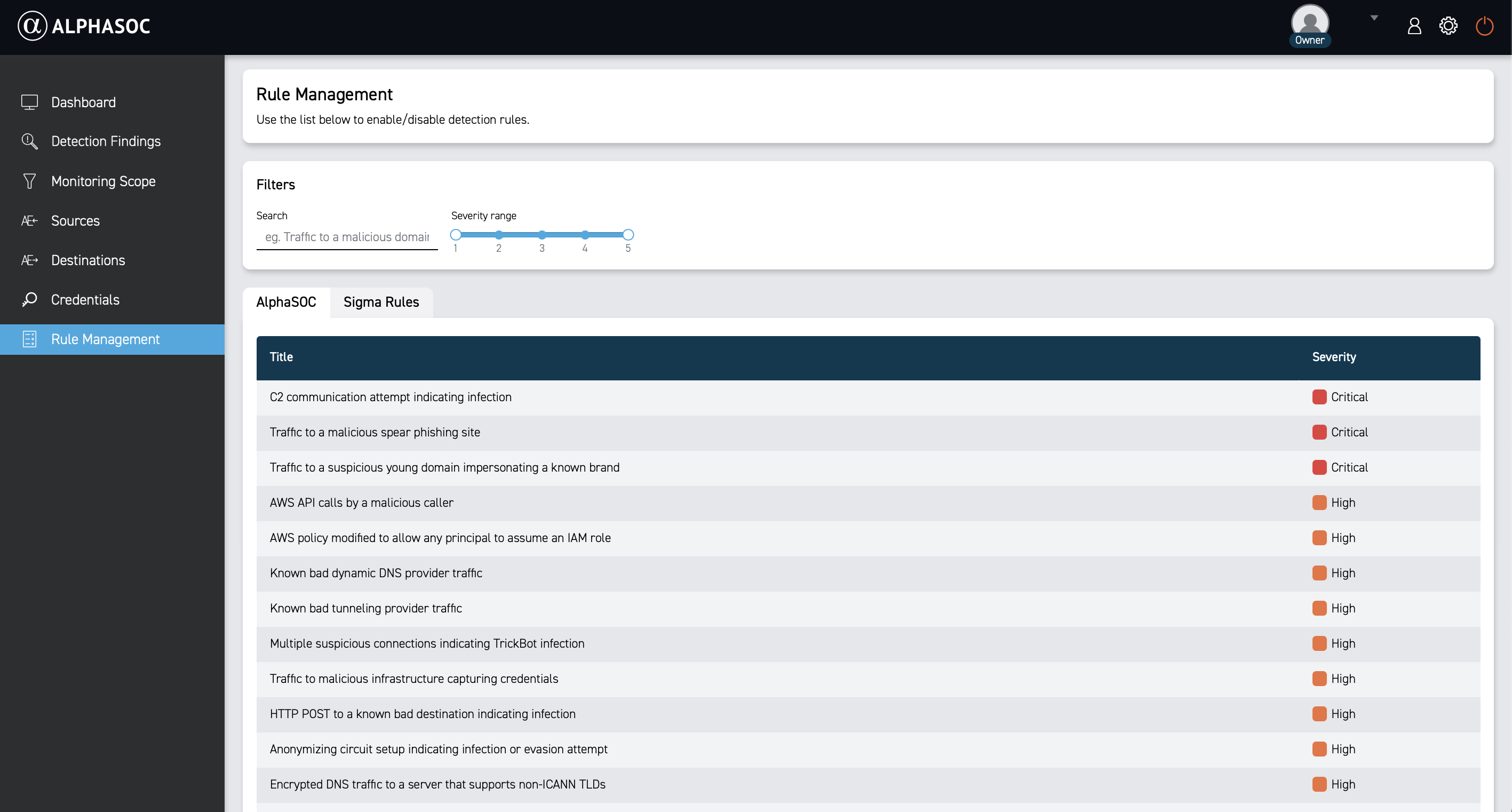
AlphaSOC Detections
AlphaSOC provides a wide variety of high-quality detections out of the box, designed to identify threats and anomalies across diverse environments. These detections are supported across many data origins, including cloud platforms (e.g., AWS, Azure, GCP), SaaS applications (e.g., Okta, GitHub), endpoints (e.g., CrowdStrike, SentinelOne), network sensors (e.g., Zeek, Suricata), and more. They leverage behavioral analysis, threat intelligence, and anomaly detection to surface both known and novel threats with minimal configuration. Click here to see the full list of available AlphaSOC detections.
Sigma Rules
AlphaSOC natively supports Sigma Rules, enabling users to enhance detection capabilities with custom rules tailored to their environment. These rules can be added manually through the AlphaSOC web console or imported programmatically via our API, providing flexibility for seamless integration and automation.
The Sigma Rules section lists each rule with its title, severity, status, enabled state, and available actions (edit, delete).
Use filters to narrow down the list of Sigma rules by:
- Name
- Severity
- Status (stable, test, experimental, deprecated, unsupported)
- Enabled (true or false)
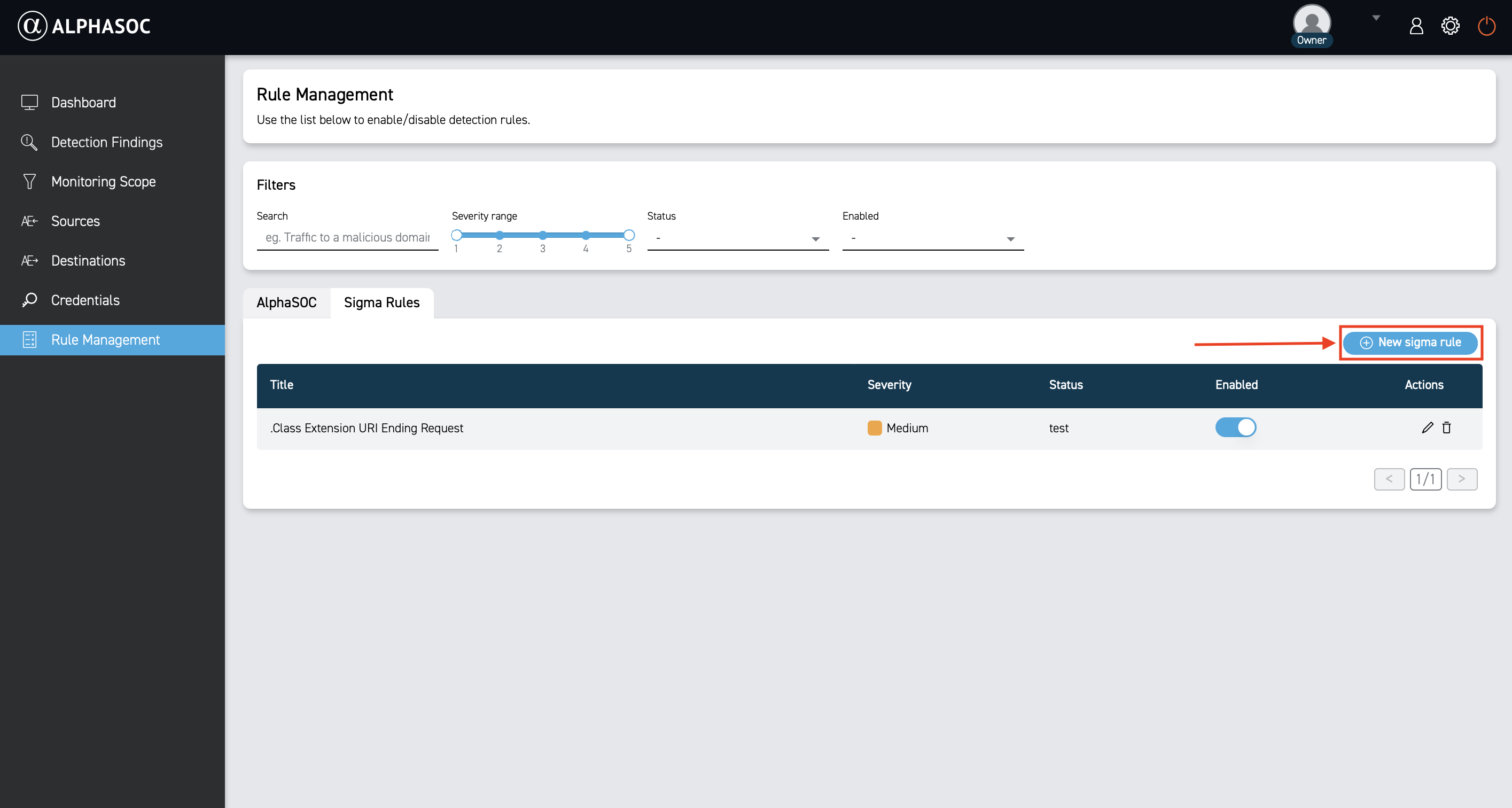
Adding Custom Sigma Rules
To add a custom Sigma rule:
- Click New sigma rule.
- Paste or write the Sigma rule.
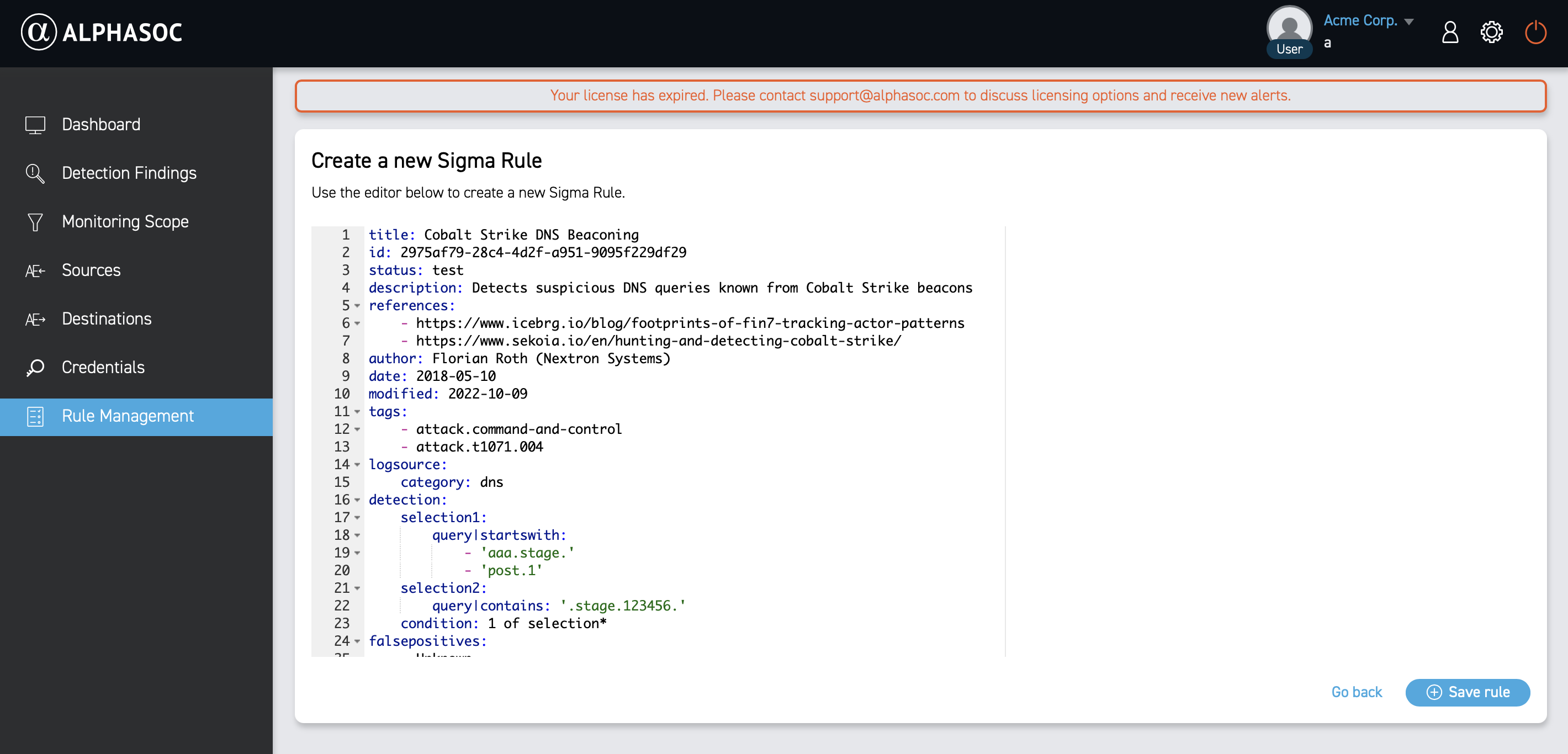
- Click Save rule.
After saving, the custom rule appears in the Sigma Rules section.
Managing Sigma Rules
Use the Actions column to edit or delete an existing rule. Toggle the switch in the Enabled column to activate or deactivate the rule.