Detection Findings
The Detection Findings page provides insights into findings generated by AlphaSOC. Use it to filter, visualize, and review findings to identify potential security incidents in your environment.
Filters
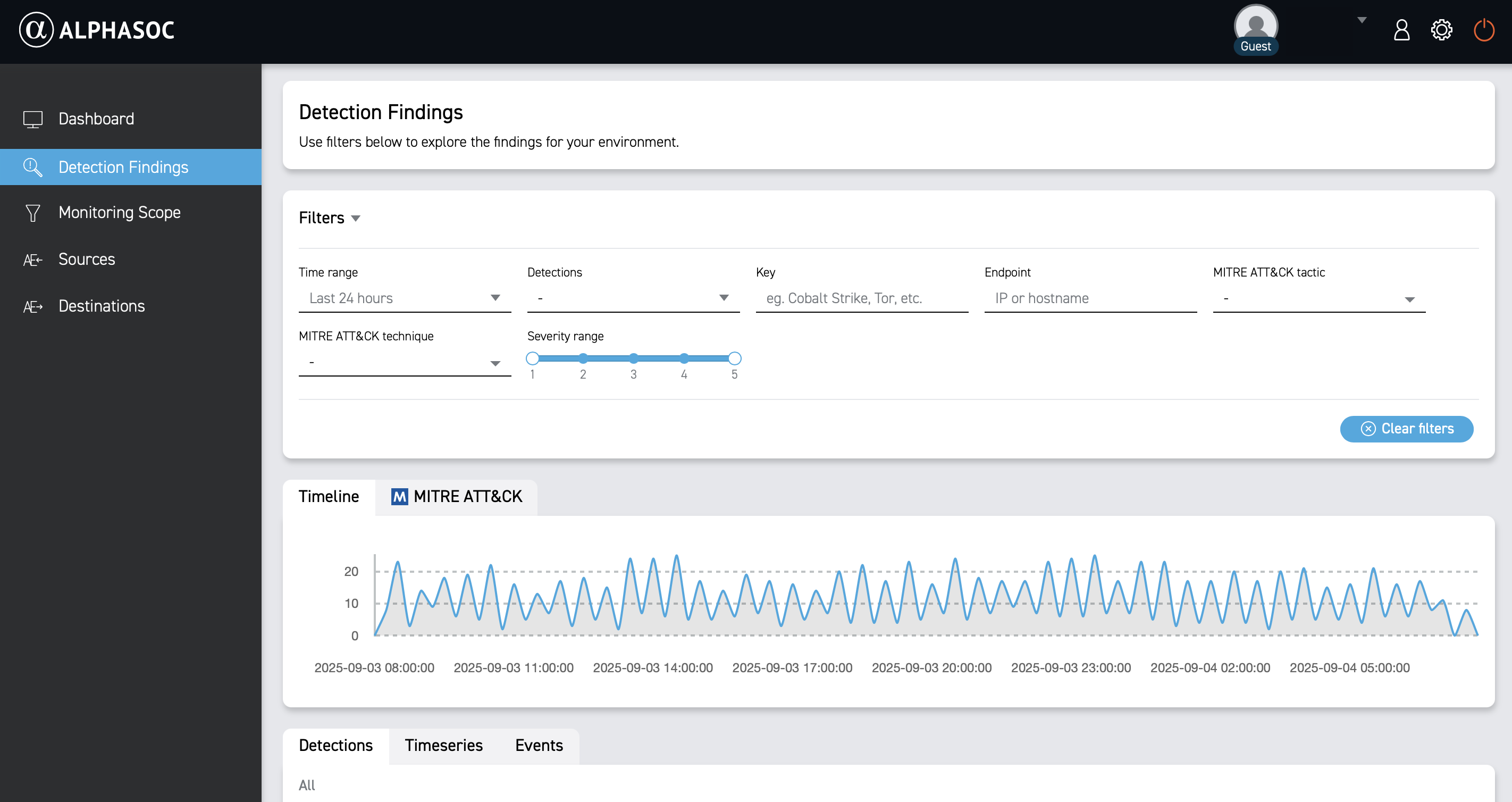
To reduce noise and focus on the most relevant findings, narrow the results by applying filters.
Available filters include:
- Time range: Select a predefined range or set a custom range using the date picker.
- Detections: Select or search for specific detection names. View the full catalog here.
- Key: Search for a malware family, adversarial tool (e.g., Cobalt Strike), or keyword (e.g., Tor).
- Endpoint: Search for a hostname, IP address, MAC address, or third‑party account identifier to see related findings.
- MITRE ATT&CK® tactic: Select one or more tactics to filter by attack patterns.
- MITRE ATT&CK® technique: Select one or more techniques to filter by specific methods.
- Severity range: Select severity levels from 1 (informational) to 5 (critical) by sliding the handles on the bar.
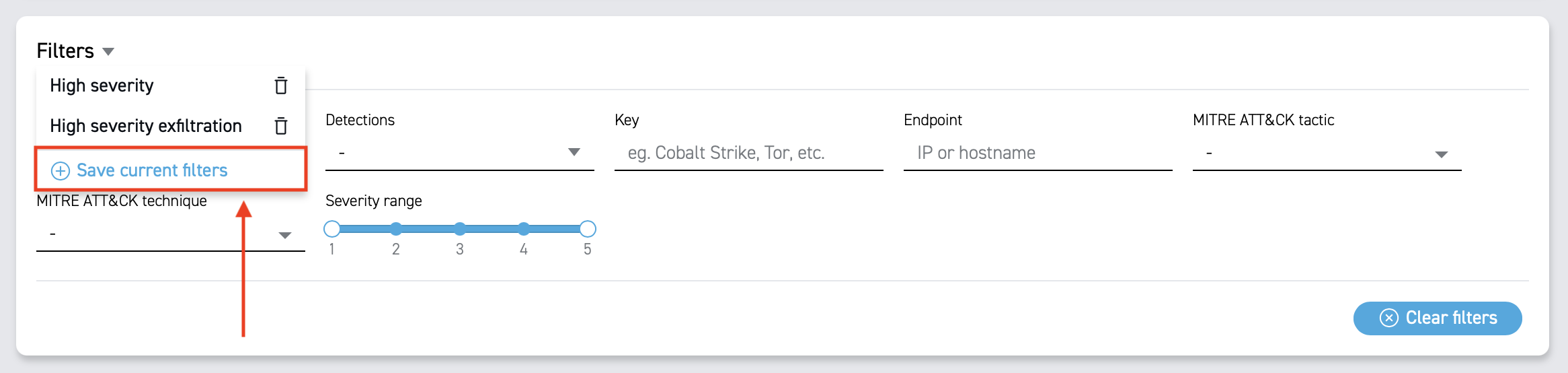
Creating and Managing Filters
You can save frequently used filter combinations for quick access in the future. To do so, apply the desired filters, click on the down-pointing arrow next to the Filters. You will then see the Save current filters button at the bottom of the list.
User or Owner permissions are required to save and delete filters. An
Owner is also able to create and manage organization-wide filters.
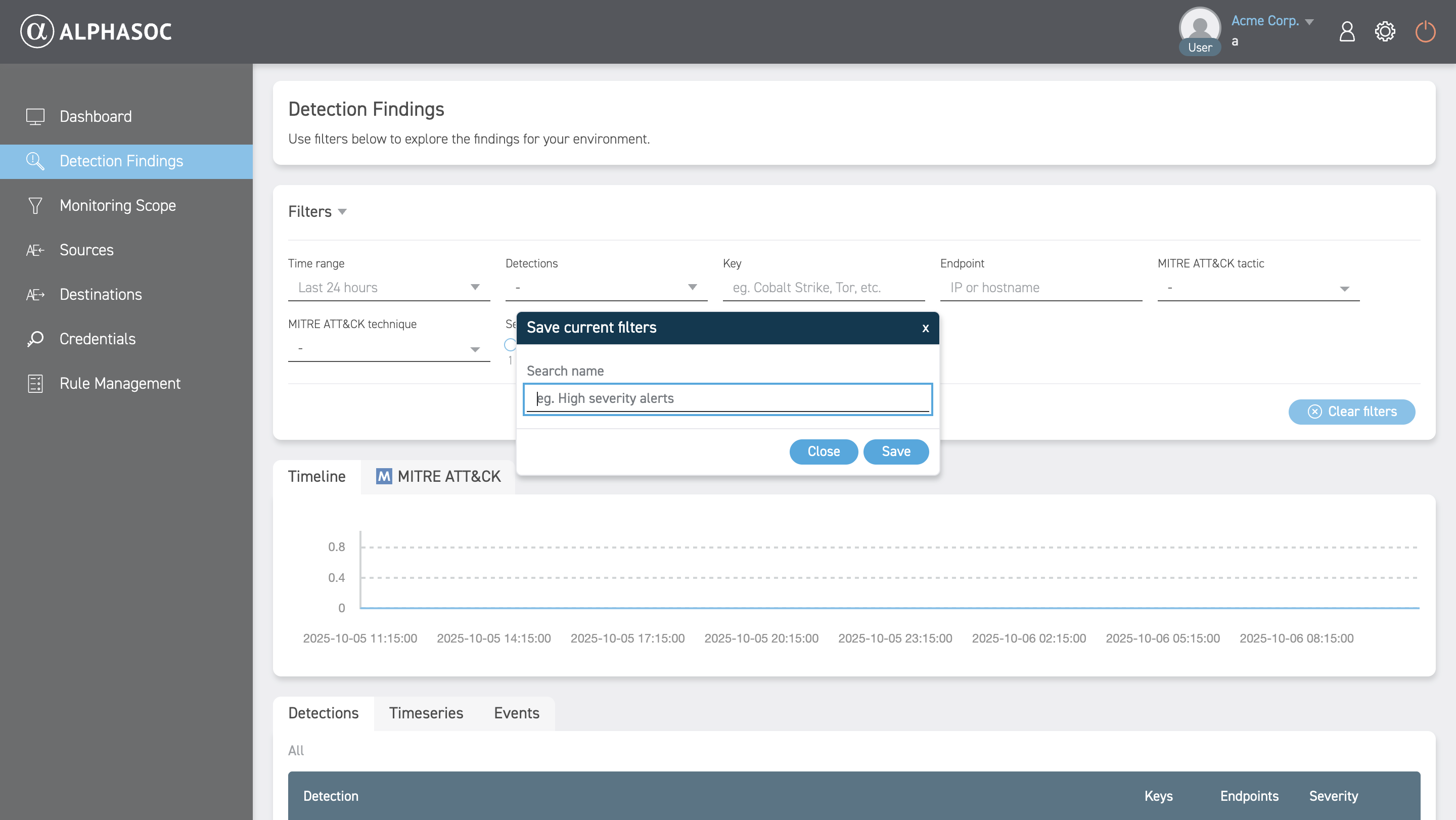
When you save a filter set, you are prompted to name it.
As an Owner, you can create organization‑wide filters accessible to all users
in your organization. To do this, toggle Make it public for users of this
organization.
Once saved, the filter appears in the dropdown list for easy access. If you no longer use a saved filter, you can delete it by clicking the delete icon next to it.
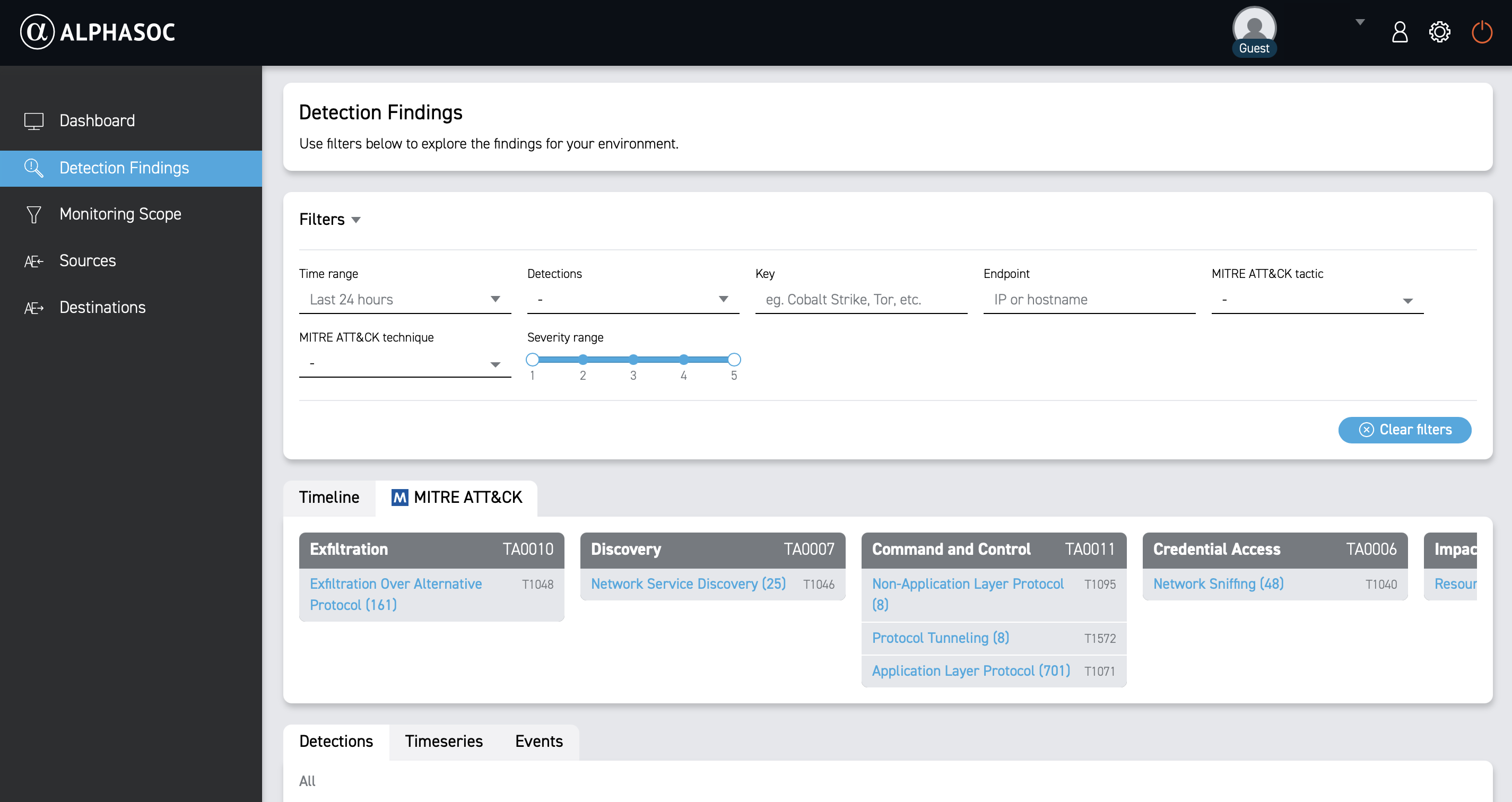
Findings Views
To better understand your security landscape, use the Timeline and MITRE ATT&CK® views to visualize detection patterns.
Timeline
The Timeline view shows when detections occurred, helping you spot trends or spikes that may indicate ongoing attacks or persistent threats.

MITRE ATT&CK®
The MITRE ATT&CK® view organizes detections by MITRE ATT&CK® tactics and techniques so you can identify common attack patterns and prioritize response.
Reviewing Findings
At the bottom of the Detection Findings page, review the list of findings that match your filters. Each finding displays key details based on the selected tab: Detections, Timeseries, or Events.
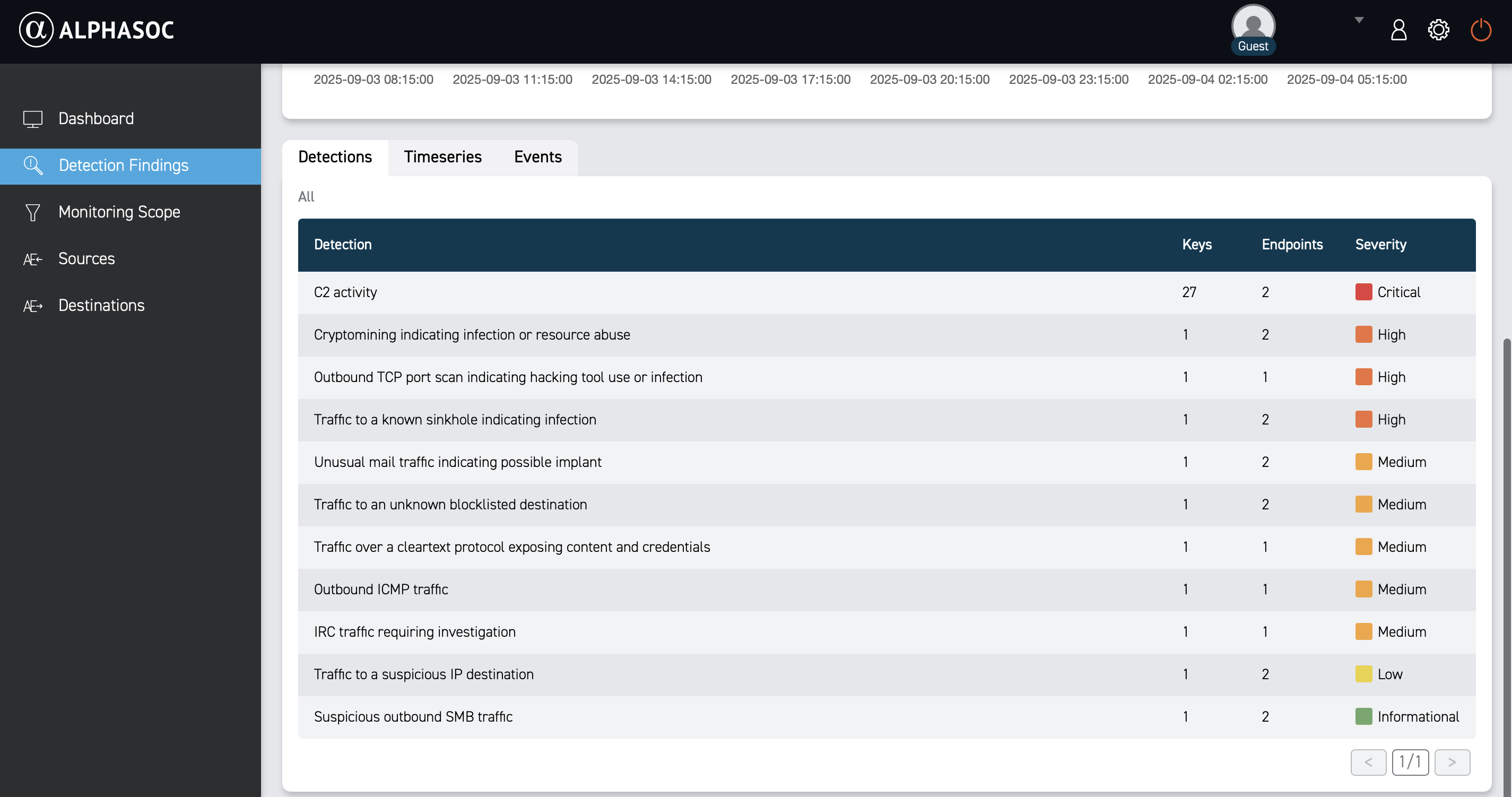
Detections
The Detections view shows a summary: detection name, severity, number of endpoints involved, and keys matching your filters. Click a finding for more details.
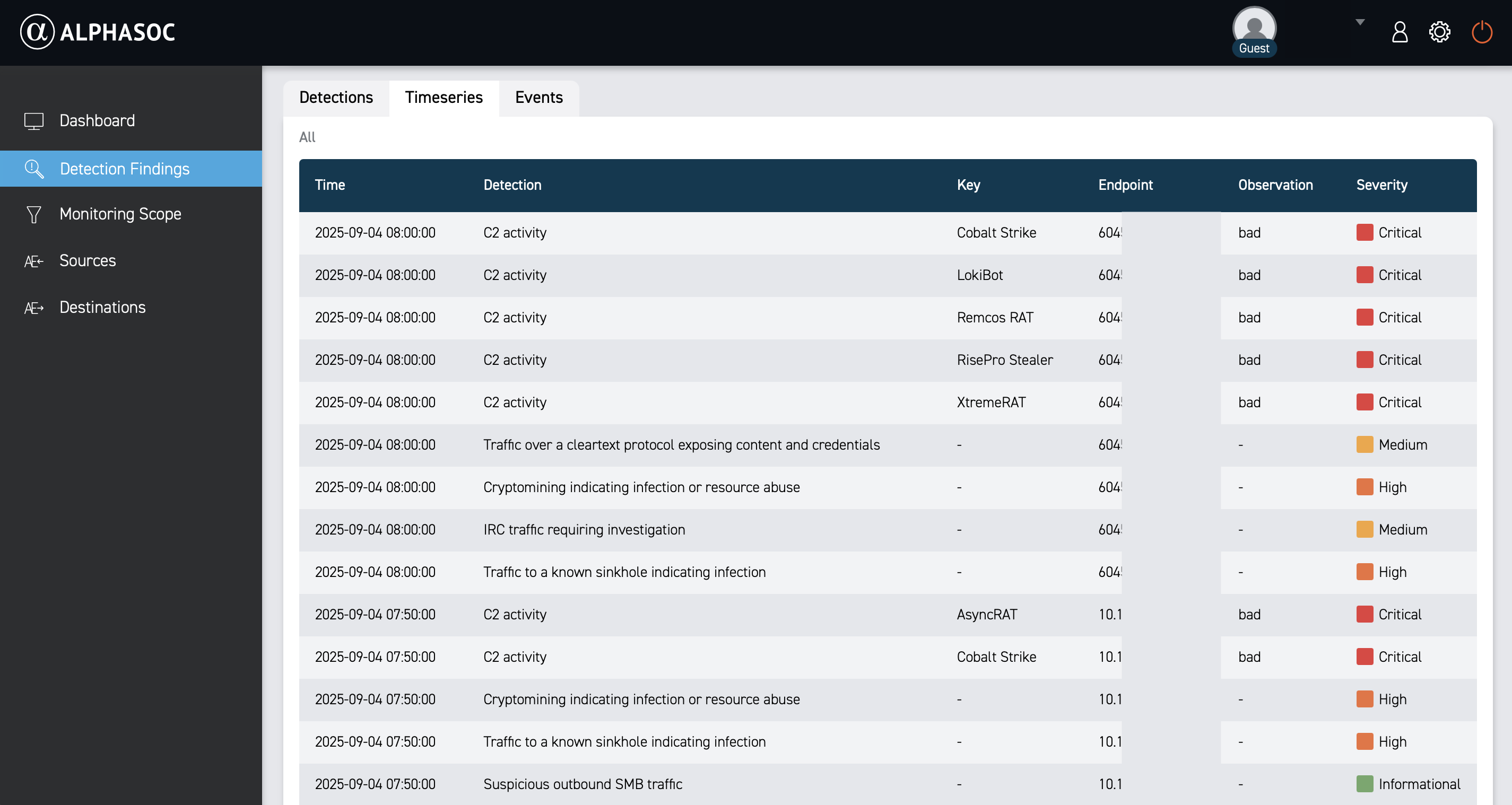
Timeseries
The Timeseries view provides a chronological timeline of events associated with the finding (most recent first). This view helps you understand the sequence of events and aids in incident investigation. It includes detection name, keys, endpoints, observations, and severity.
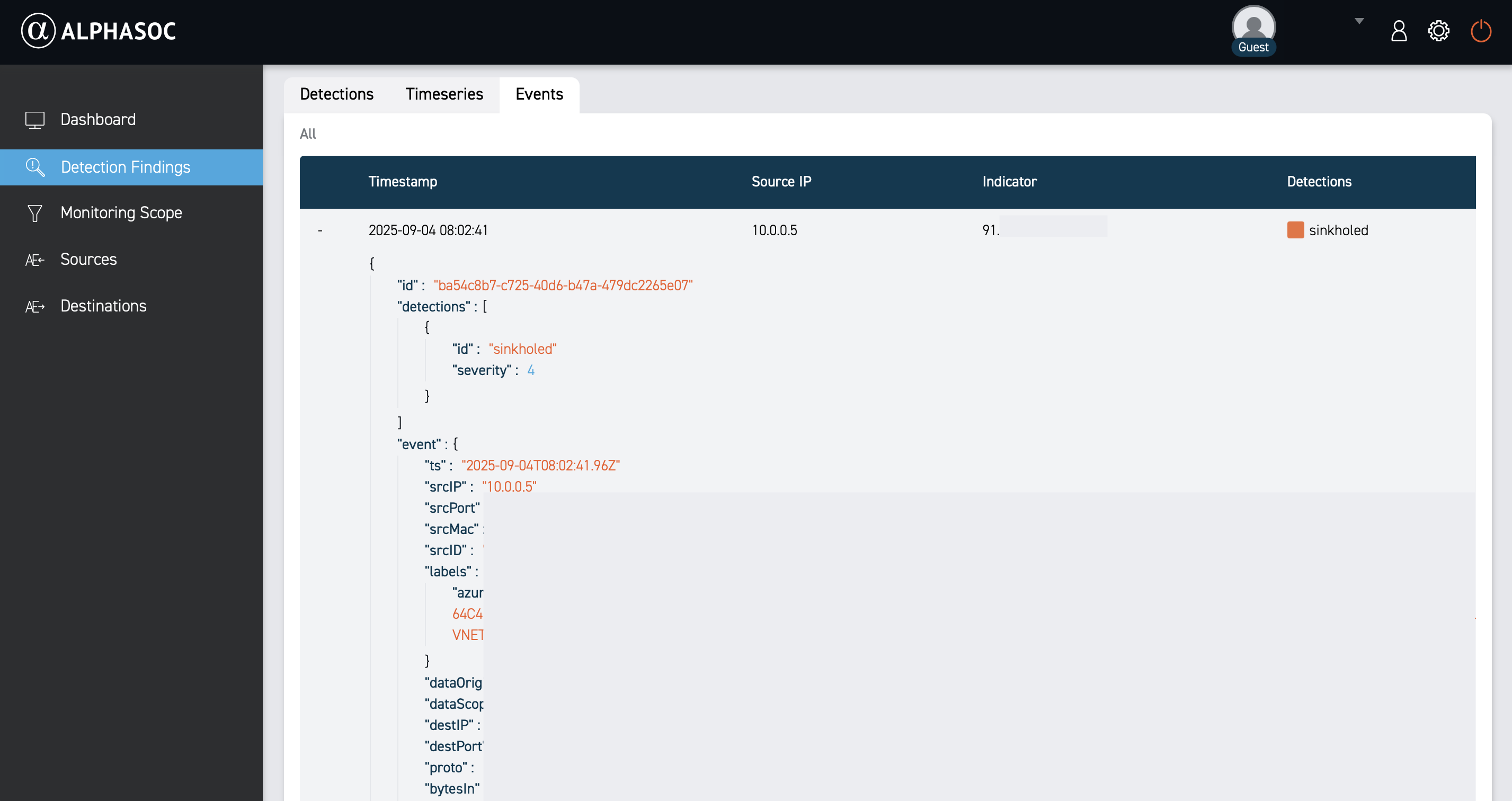
Events
The Events view lists individual events that triggered the detection. This view is useful for deep-dive investigations and forensics, as it provides the raw data that triggered the detection.
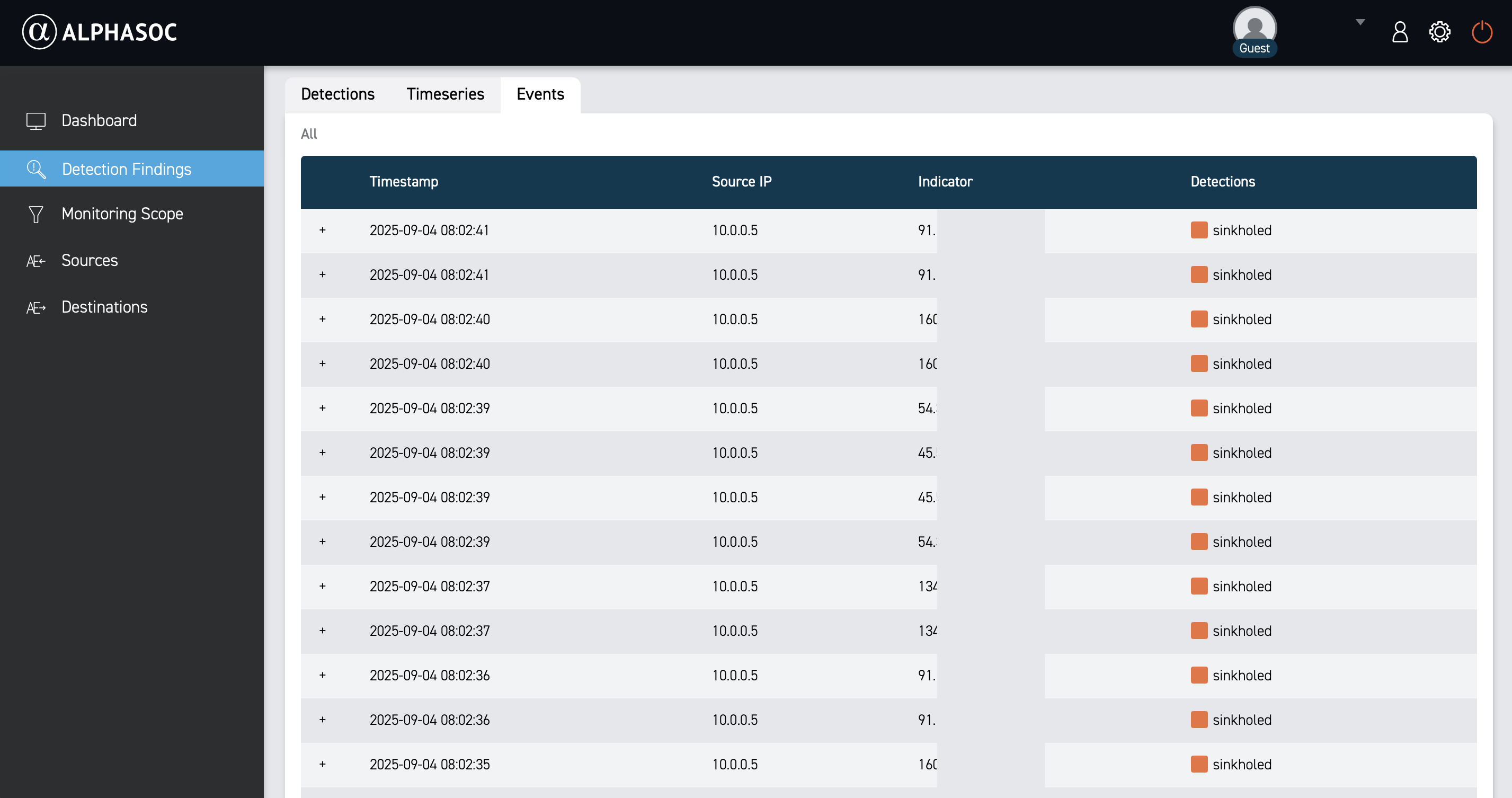
Each event includes a timestamp, event type, source IP, indicator, and detection names. Click the plus icon next to an event to view full log details in JSON.