Sigma Correlations
What are Sigma Correlations?
This feature is currently in closed beta and will be released to all users soon.
Sigma correlations aggregate multiple related events over a specified time window to identify complex attack patterns that involve multiple steps or stages, which may not be apparent when looking at individual events in isolation. They enable you to define relationships between events generated by Sigma rules, helping detect sophisticated threats that could otherwise go unnoticed.
Correlation structure
A Sigma correlation is specified in the correlation section and includes the
following fields: type, rules, group-by, timespan, and condition.
Where:
type - The type of correlation (see
Supported Sigma Correlations).
rules - A list of Sigma rules (name or ID) to be
correlated.
group-by - Fields used to group the events.
timespan - The time window for correlation.
condition - The condition that must be met for the
correlation to trigger (see Comparison operators).
AlphaSOC allows you to add optional tags (for MITRE ATT&CK mapping) and name
fields to correlations. MITRE ATT&CK tags must follow
Sigma naming convention.
Let's look at an example of a Sigma correlation below:
title: Potential Reconnaissance For Cached Credentials Via Cmdkey.EXE
id: 07f8bdc2-c9b3-472a-9817-5a670b872f53
name: windows_cmdkey_recon
status: test
description:
Detects usage of cmdkey to look for cached credentials on the system
author:
jmallette, Florian Roth (Nextron Systems), Nasreddine Bencherchali (Nextron
Systems)
tags:
- attack.credential-access
- attack.t1003.005
logsource:
category: process_creation
product: windows
detection:
selection_img:
- Image|endswith: '\cmdkey.exe'
- OriginalFileName: "cmdkey.exe"
selection_cli:
CommandLine|contains|windash: " -l"
condition: all of selection*
falsepositives:
- Legitimate administrative tasks
level: low
---
title:
Multiple Cmdkey.EXE Executions Indicating Cached Credential Reconnaissance
id: 921f3b51-4ef9-4ca3-82e5-b4b7805d0ba4
name: windows_cmdkey_recon_multiple
This example defines a correlation named windows_cmdkey_recon_multiple that
triggers when the windows_cmdkey_recon rule fires 5 or more times for the same
user within a 10-minute window, indicating potential reconnaissance for cached
credentials.
Adding Sigma Correlations
You can add Sigma correlations to AlphaSOC using either the AlphaSOC console or the API.
Using the AlphaSOC Console
To add Sigma correlations through the AlphaSOC console:
-
Navigate to Rule Management > Sigma Rules page.
-
Click New sigma rule.
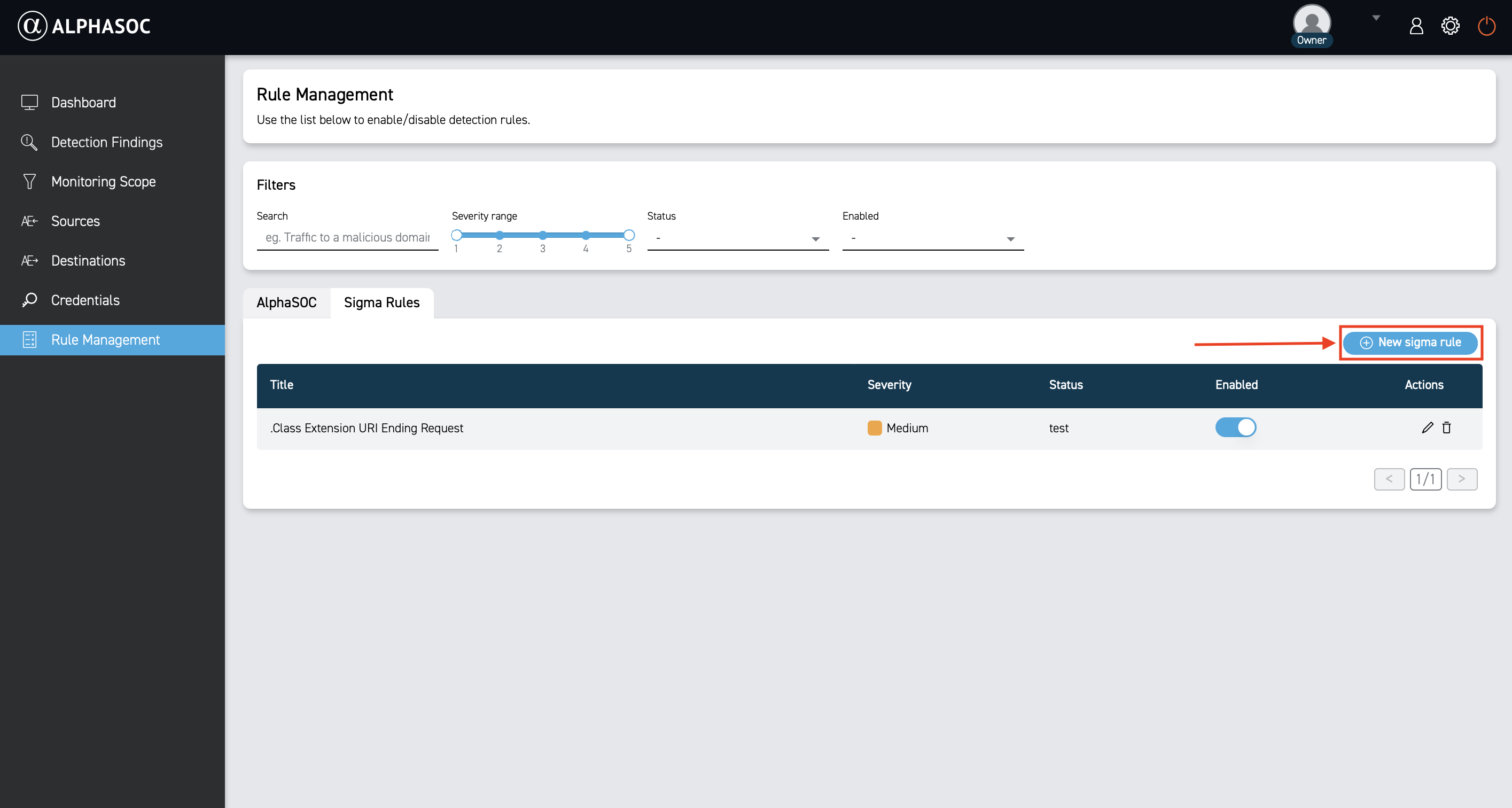
- Paste or write a Sigma correlation.
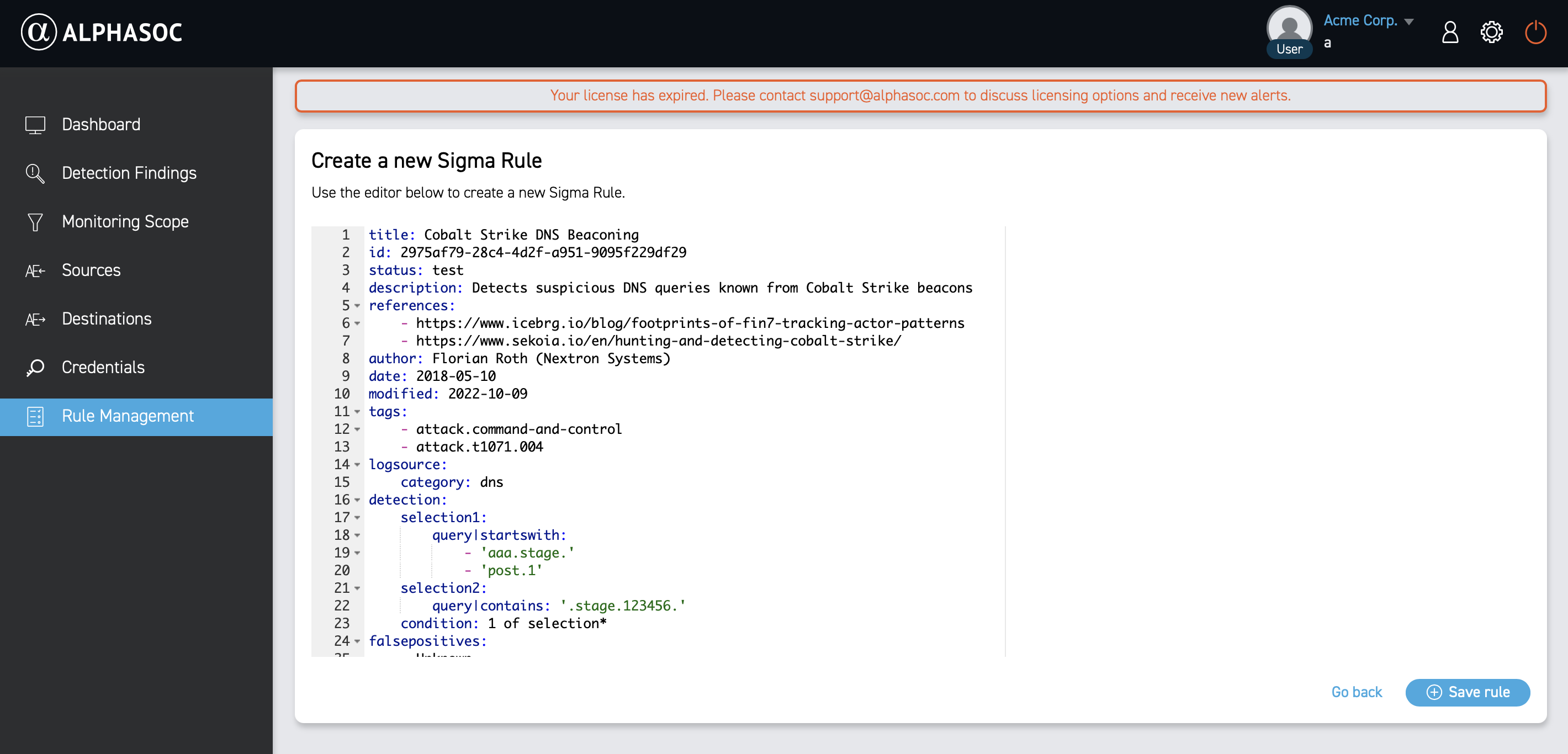
- Click Save rule.
Using the API
You can upload Sigma rules to AlphaSOC via our Detection management API.
Supported Sigma Correlations
| Type (event_type) | AlphaSOC Support |
|---|---|
event_count | SUPPORTED |
value_count | SUPPORTED |
value_sum | SUPPORTED |
value_avg | SUPPORTED |
value_percentile | NOT SUPPORTED |
temporal | SUPPORTED |
ordered_temporal | NOT SUPPORTED |
Correlation fields
AlphaSOC cannot support all Sigma features at this moment, which means certain field restrictions apply:
rules - Required. Must be a unique list of referenced
rules (1-20 rules allowed).
aliases - Not currently supported.
group-by - Required. Must be a unique list of fields
used for grouping (1-5 fields allowed).
timespan - Required. Time window for correlation
(minimum 1 minute, maximum 7 days).
condition - Required. Must include at least one
condition (see Comparison operators). Some operators
are not supported for certain correlation types (see individual correlation type
sections below).
Comparison operators
AlphaSOC supports the following comparison operators in Sigma correlation
condition field:
gt - Greater than (>).
gte - Greater than or equal to (≥).
lt - Less than (<).
lte - Less than or equal to (≤).
eq - Equal to (=).
neq - Not equal to (≠).
Please note that AlphaSOC architecture is different
from common SIEM platforms. AlphaSOC is a real-time analytics engine, and
therefore lt and lte operators are only supported for value_avg
correlation type.
event_count
The event_count correlation counts the number of events that match the
specified rules within the defined timespan. This is useful for detecting
patterns of repeated activity, such as multiple failed login attempts or Denial
of Service (DoS) attacks.
title: Several unsuccessful AWS console login attempts for a user
id: 0b1cdcb9-8170-4c5e-983c-32e2831940b5
name: aws_console_login_failure_user
status: stable
correlation:
type: event_count
rules:
- aws_console_login_failure
group-by:
- userIdentity.arn
timespan: 10m
condition:
gte: 5
tags:
- attack.credential-access
- attack.t1110
level: medium
Valid comparison operators: eq, gt, gte.
value_count
The value_count correlation counts the number of distinct values in specified
fields over the given timespan. This is useful for detecting anomalies involving
many unique occurrences, such as brute force attacks or reconnaissance.
title: High number of GitHub repositories cloned
id: 50509146-108a-4f4d-b503-40d8ed07acff
status: test
correlation:
type: value_count
rules:
- b4354cde-0ced-44a7-a653-88639da38ca8
group-by:
- actor_id
timespan: 1h
condition:
field: repository_id
gte: 5
level: high
field requires 1-5 values for correlation. Valid comparison operators: eq,
gt, gte.
value_sum
The value_sum correlation sums the numeric values of a specified field over
the defined timespan. This is useful for aggregating total amounts, such as the
total data transferred.
title: High volume of outbound traffic over SSH
id: e0f7d63f-3d1a-4595-ac95-c774e201b54d
name: high_volume_ssh
status: stable
correlation:
type: value_sum
rules:
- ssh_outbound
group-by:
- src_ip
timespan: 1h
condition:
field: bytes_out
gt: 1000000
level: medium
field requires exactly 1 value. Valid comparison operators: eq, gt, gte.
value_avg
The value_avg correlation calculates the average of numeric values in a
specified field over the defined timespan. This is useful for finding average
metrics, such as average data transferred per time frame.
title: Unexpected average network traffic
id: 75adaa6c-3f8c-4f3e-8384-5341e5478bdc
status: stable
correlation:
type: value_avg
rules:
- a0d6ad27-9eff-4b6e-b68f-5d92be12f1d2
group-by:
- src_ip
timespan: 24h
condition:
field: bytes_out
gte: 50000
field requires exactly 1 value. Valid comparison operators: eq, gt, gte,
lt, lte.
temporal
The temporal correlation looks for multiple distinct event types occurring
close together in time. This is useful for detecting complex attack patterns
that involve multiple steps.
title: AWS access key created for a newly registered IAM user
id: 3269cacb-2a8e-41c6-bd3e-e6dc957c4e3b
status: stable
correlation:
type: temporal
rules:
- aws_iam_user_created
- aws_access_key_created
group-by:
- requestParameters.userName
timespan: 12h
level: low