Microsoft Entra ID
Overview
This guide provides step-by-step instructions for configuring the Microsoft Entra ID (formerly Azure Active Directory) integration with AlphaSOC.
In this process, you'll learn how to register an application in Microsoft Entra ID, grant it necessary permissions, and establish federated credential authentication. This configuration will enable AlphaSOC to access and retrieve audit logs from your environment.
Creating App Registration
The following steps outline how to register an application and add Federated
Credentials to Microsoft Entra ID.
-
Register an application
Sign in to the Microsoft Entra ID admin center, browse to App registrations and select New registration. Enter a Display Name and select access for the accounts in this organizational directory only (Single Tenant):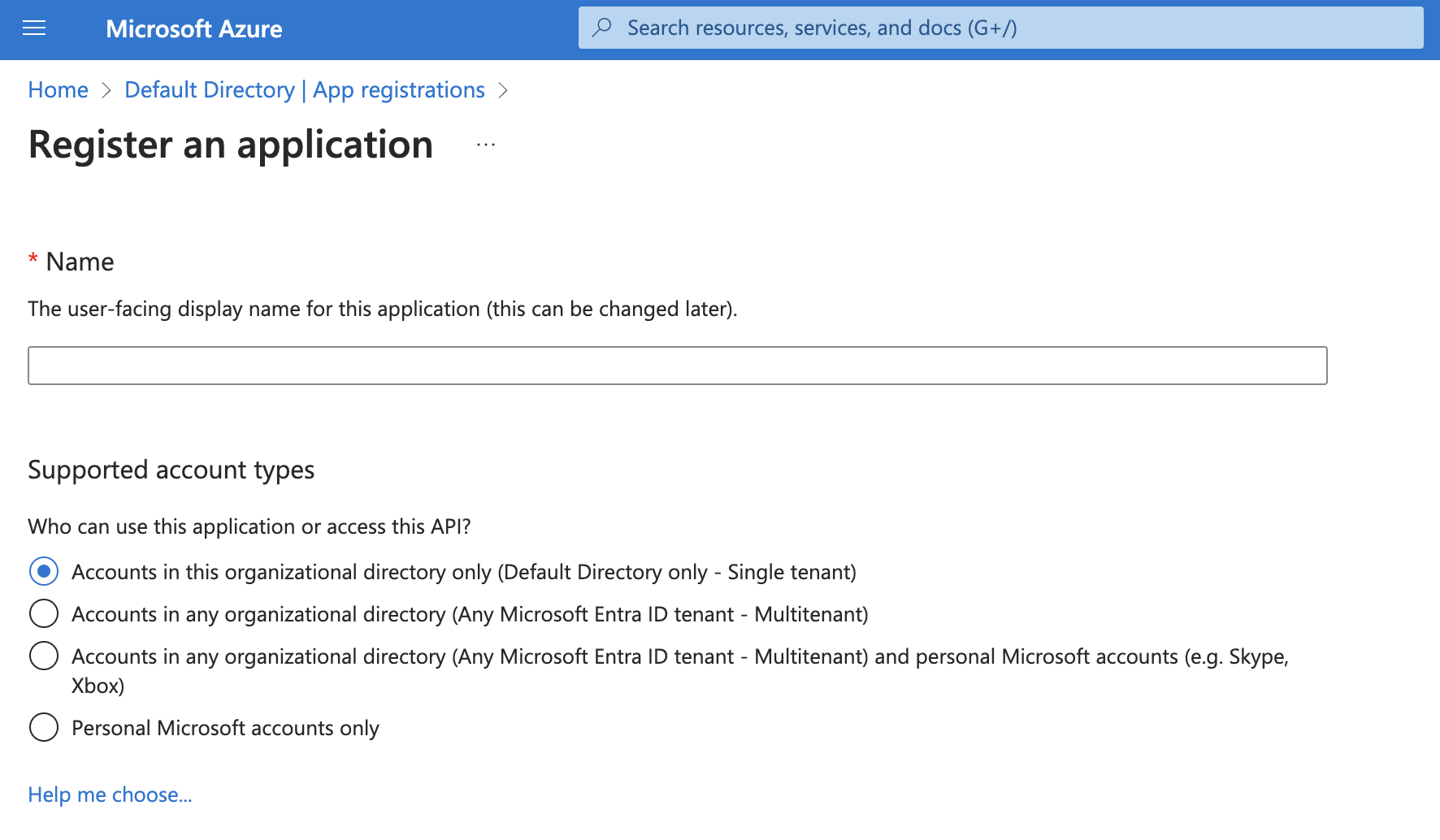
-
Add credentials to Microsoft Entra ID
Select your application in the Microsoft Entra admin center (in App registrations tab) and go to Certificates & secrets > Federated credentials > Add credential. Use the following settings:
The Issuer field cannot end with a "/".
- Federated credential scenario:
Other Issuer. - Issuer:
https://accounts.google.com. - Subject:
102911262315801235571. - Audience: your organization (workspace) ID (available in the AlphaSOC console).
- Grant permissions
Consenting to these permissions requires Privileged Role Administrator role.
Grant the newly created application AuditLog.Read.All and Directory.Read.All
permissions.
- Provide AlphaSOC with Tenant ID and Application (client) ID
If you manage multiple tenants, provide AlphaSOC with the Tenant IDs along with a list of Storage Accounts associated with each tenant.